8.6 Taiwan AI Labs Federated Validation Edge Machine Security Compliance
Taiwan AI Labs Federated Validation (FV) System follows the same security guidance as Taiwan AI Labs Federated Learning (FL) Framework.
For Taiwan AI Labs Federated Learning Edge Machine Security Compliance, please refer here.
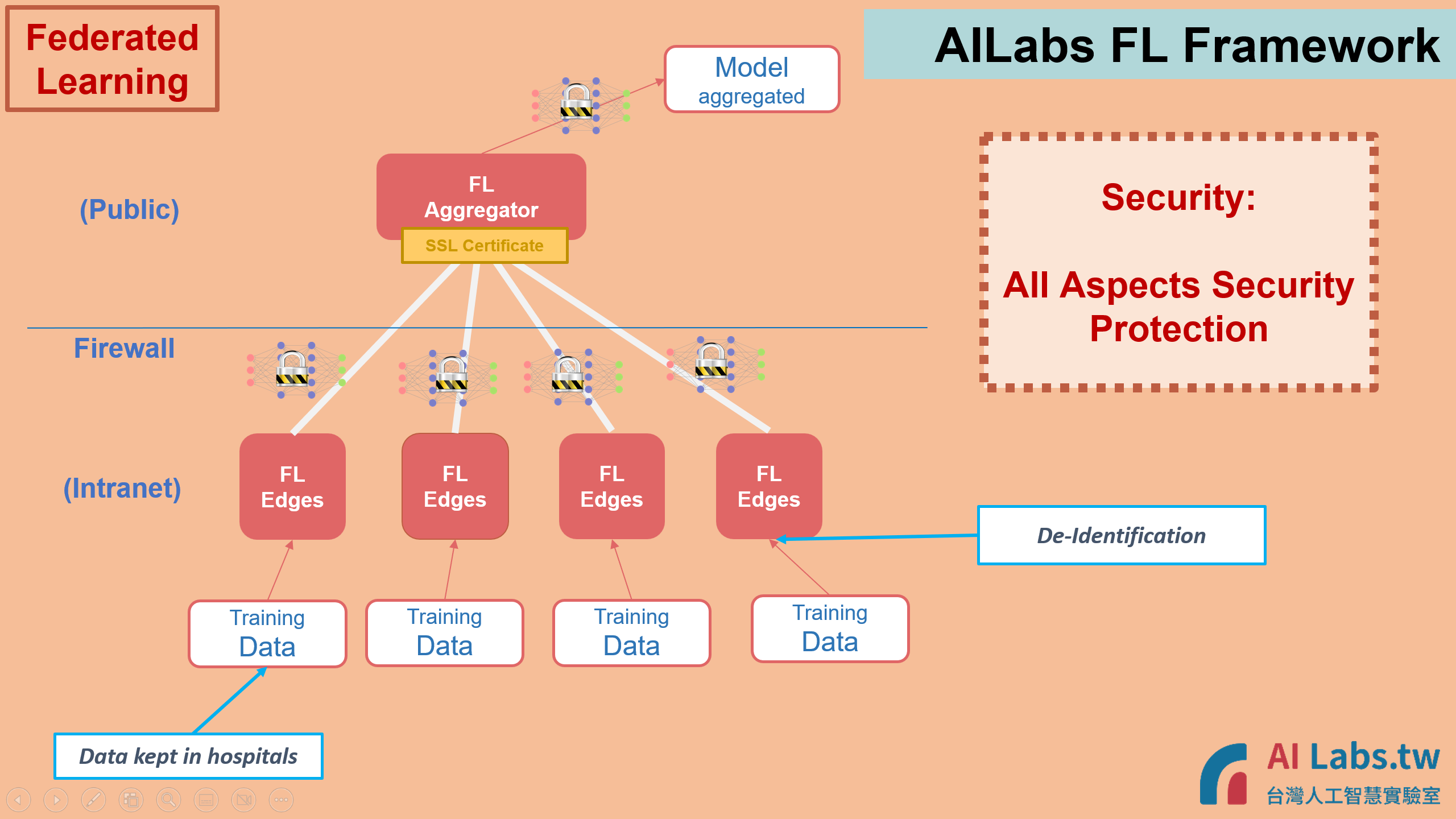
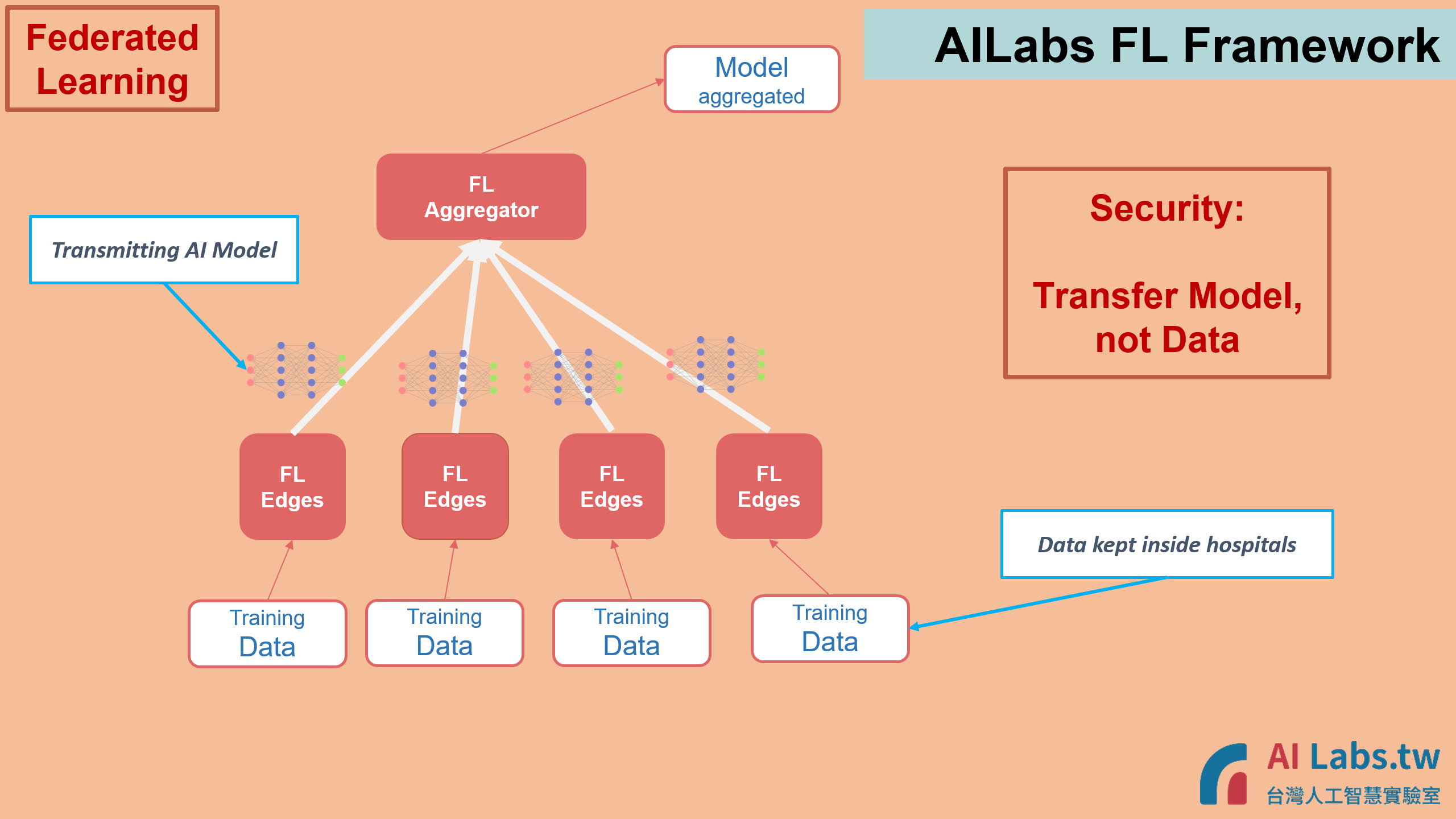
Taiwan AI Labs Federated Learning (FL) Framework contains one FL Aggregator and several FL Edges (Edge Machines). The training data is gathered inside FL Edge Machine, and AI Model is aggregated at FL Aggregator.
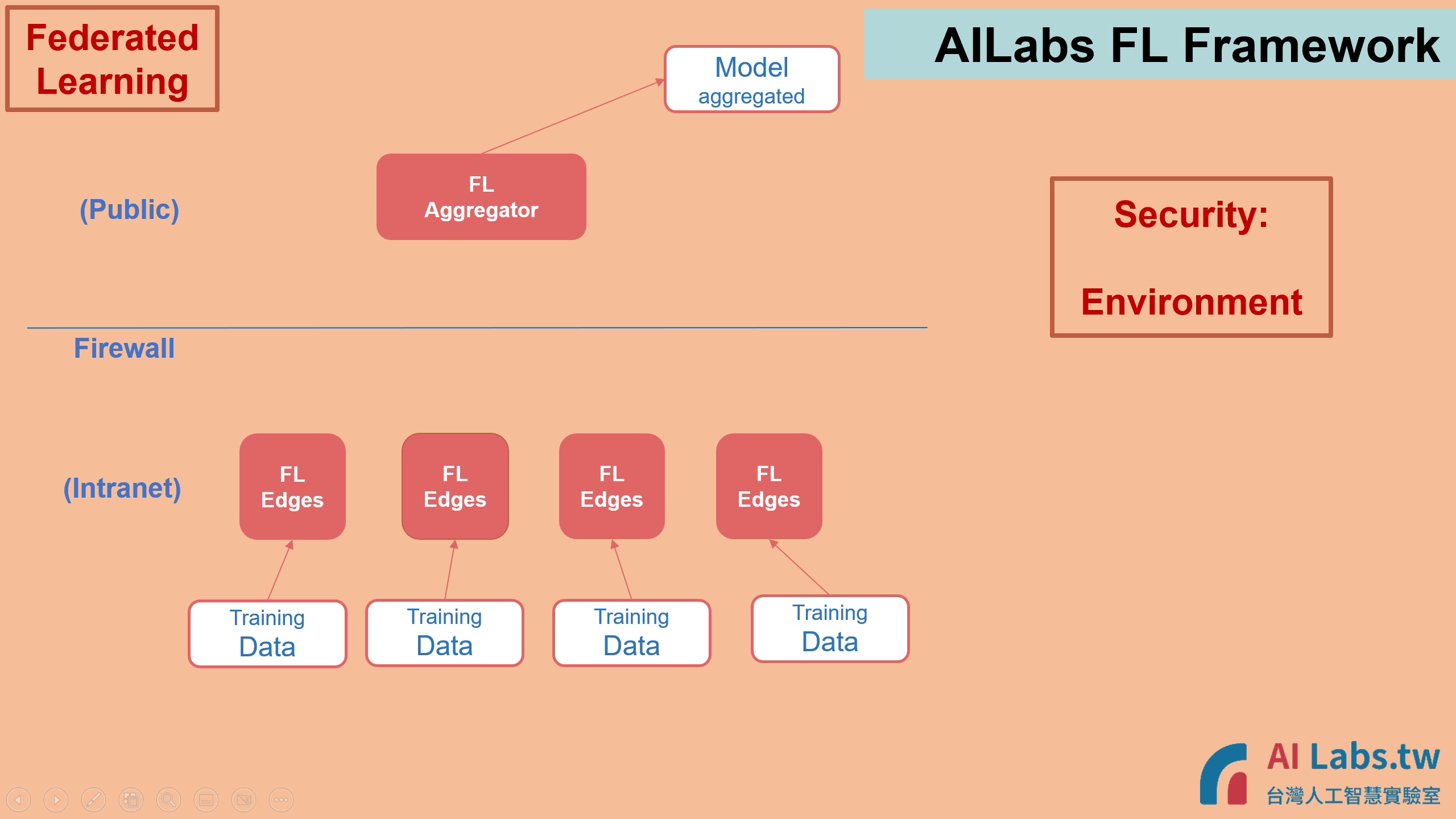
The design of Taiwan AI Labs Federated Learning Framework is to meet the security requests of Institutes completely, and to remove the possibility of data disclosure, while keeping the AI training progress efficiency. Below are the FL Framework security compliance from each aspect.
Taiwan AI Labs Federated Learning Edge Machine Security Compliance
- Taiwan AI Labs FL edge machine is designed to be located inside Institute’s private network, which means no public IP is required to assign to the Edge Machine. Without disclosing the machine on the public network, we could protect the data inside Institute’s firewall and ensure the security is following Institute's high standards.
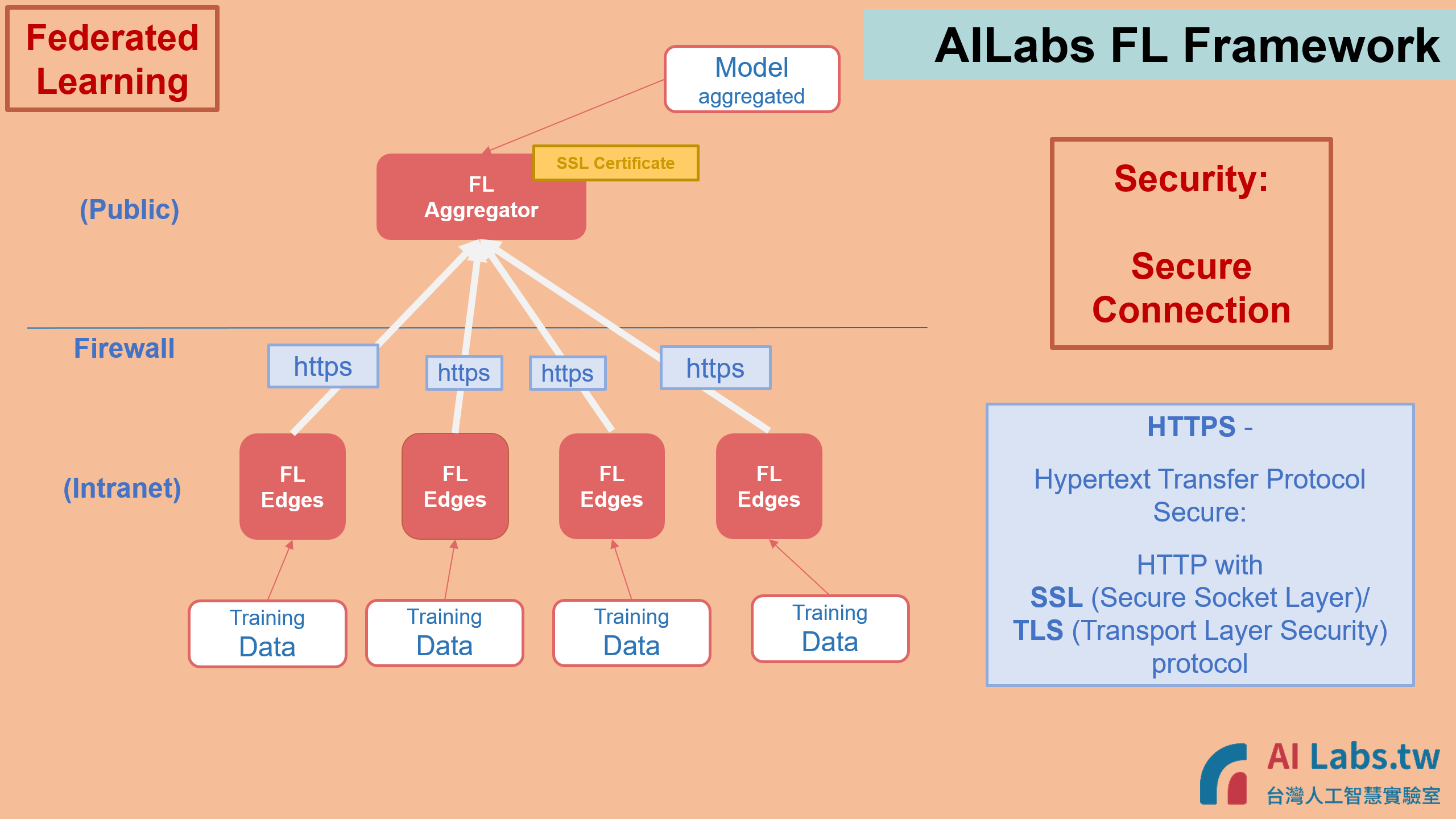
2. All transaction are transmitted through Secure Connection, following international standard.
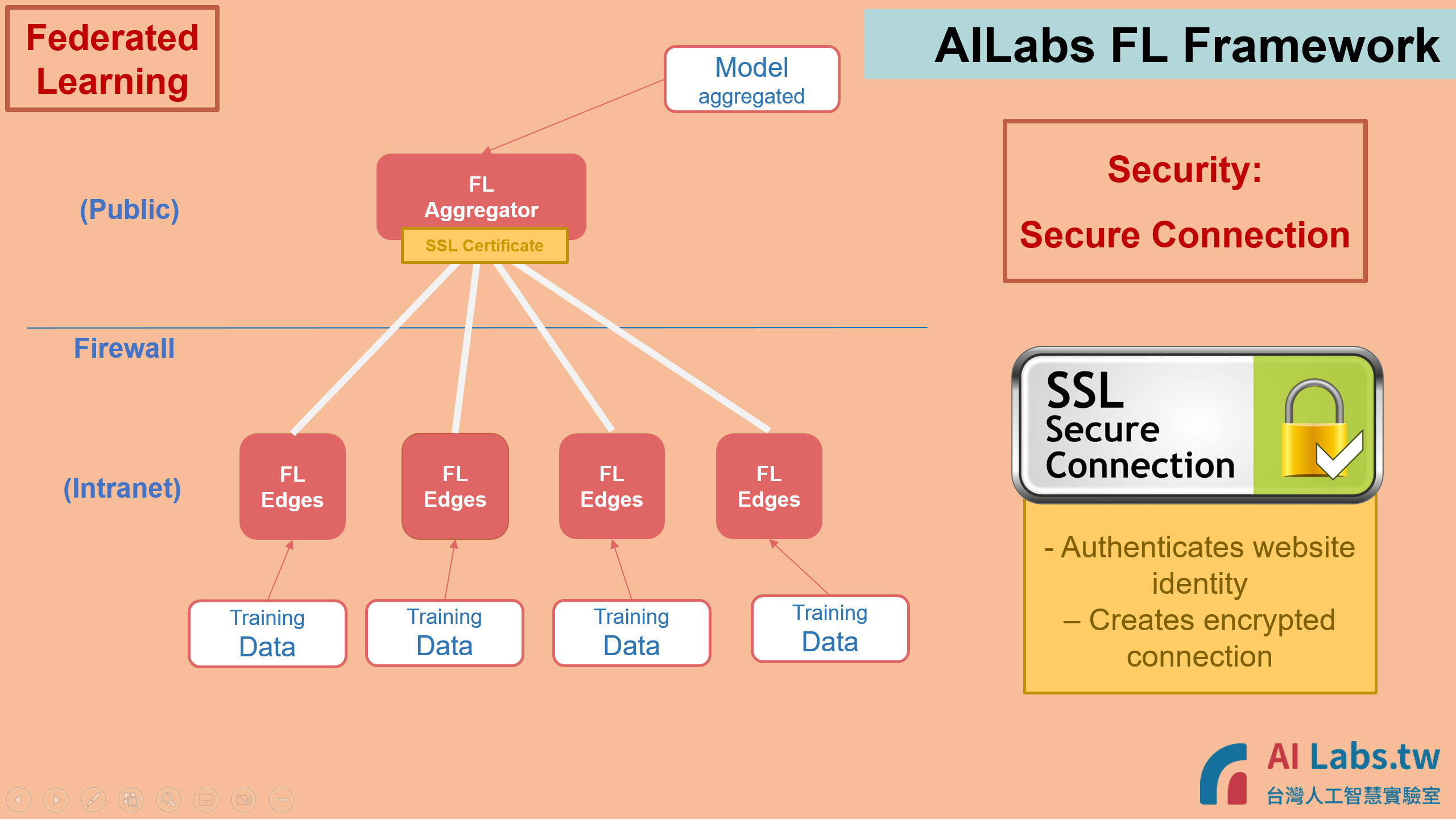
HTTPS (port 443) is the only port used during the whole process.
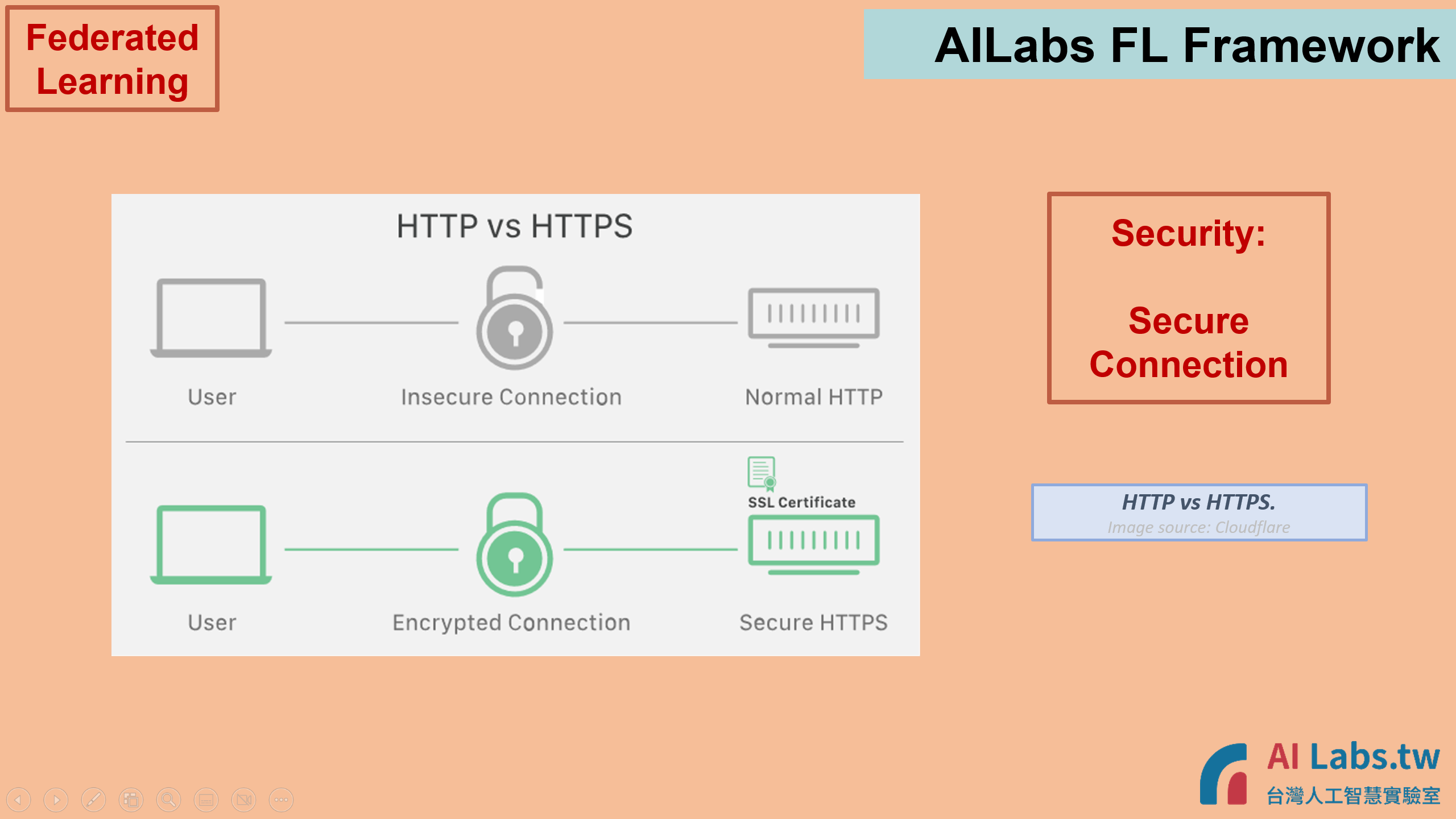
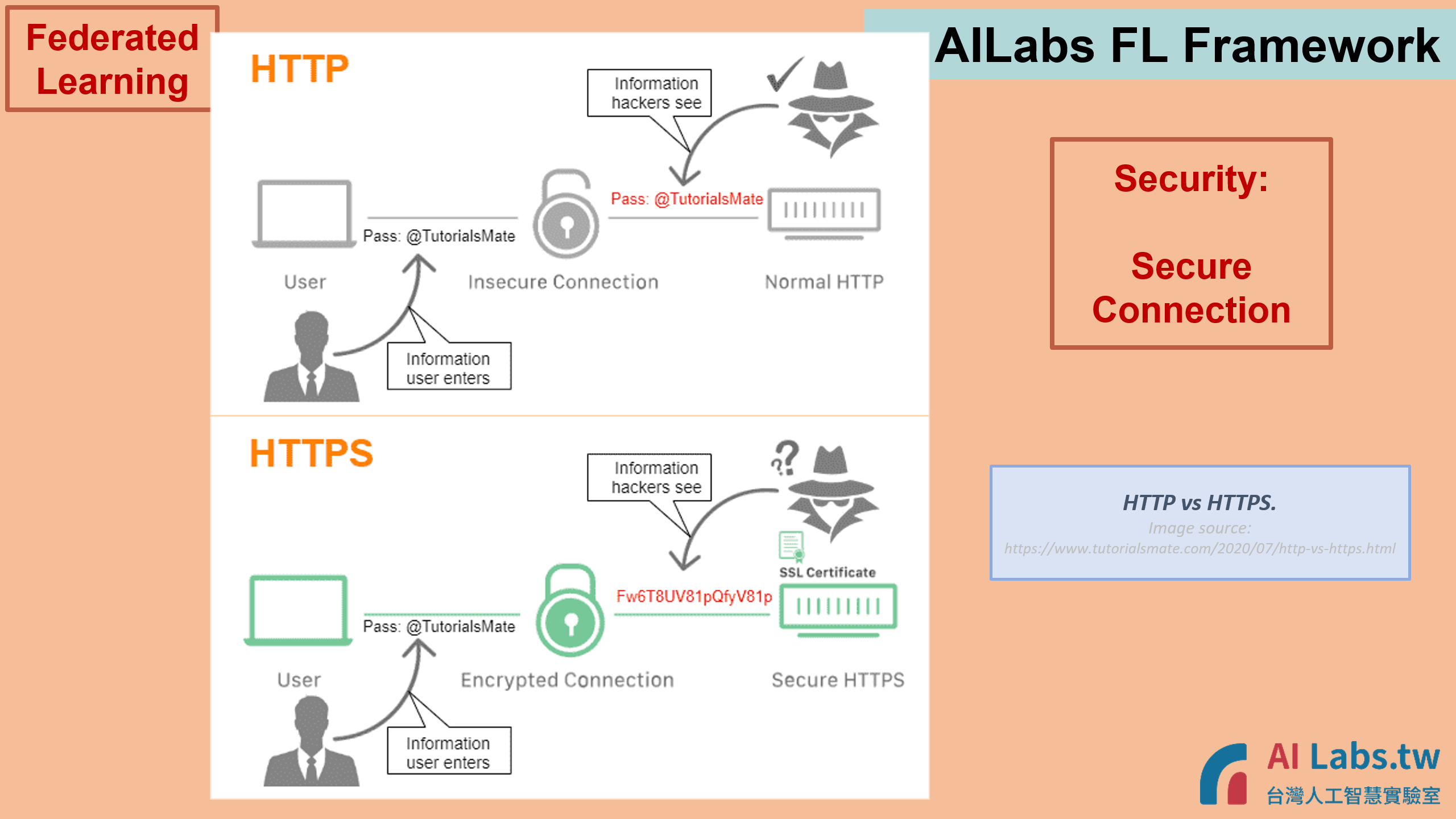
PS:
Some descriptions of HTTPS vs HTTP.
 |
 |
3. During the Federated Learning and Federated Validation progresses, only AI model and weights are transmitted. Training Datasets are kept inside Institutes, and won't be transmitted out to public domain.
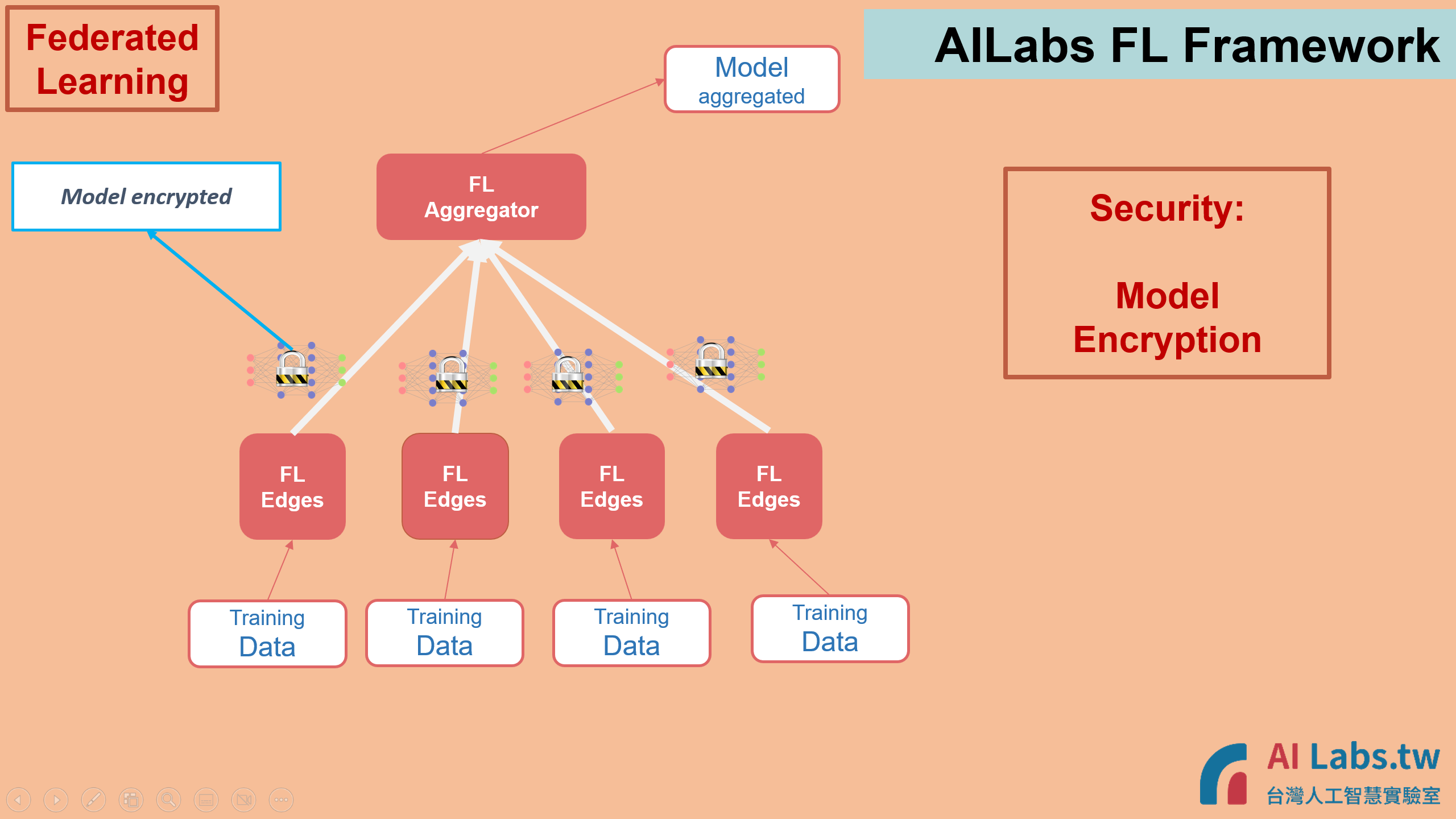
4. In addition to keep data internal and only transmit AI model weight, the model weight could be encrypted during transmission to enhance the security protection.
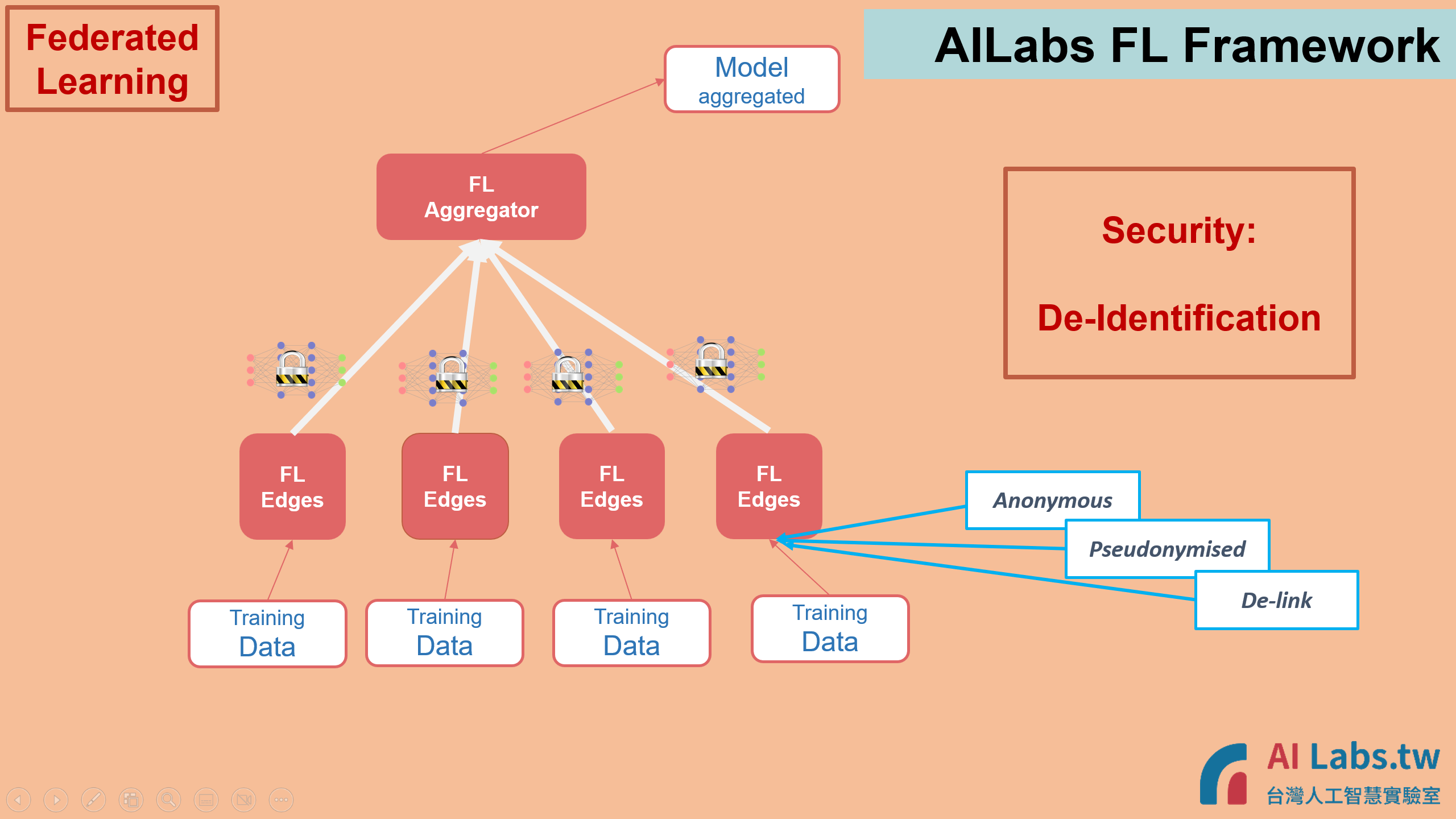
Data De-identification is ensured in the system. PI could either implement De-ID after data curation, or before data curation and run De-ID Checker later while data is ready.
5. Security affidavit letters are signed by all persons involved.

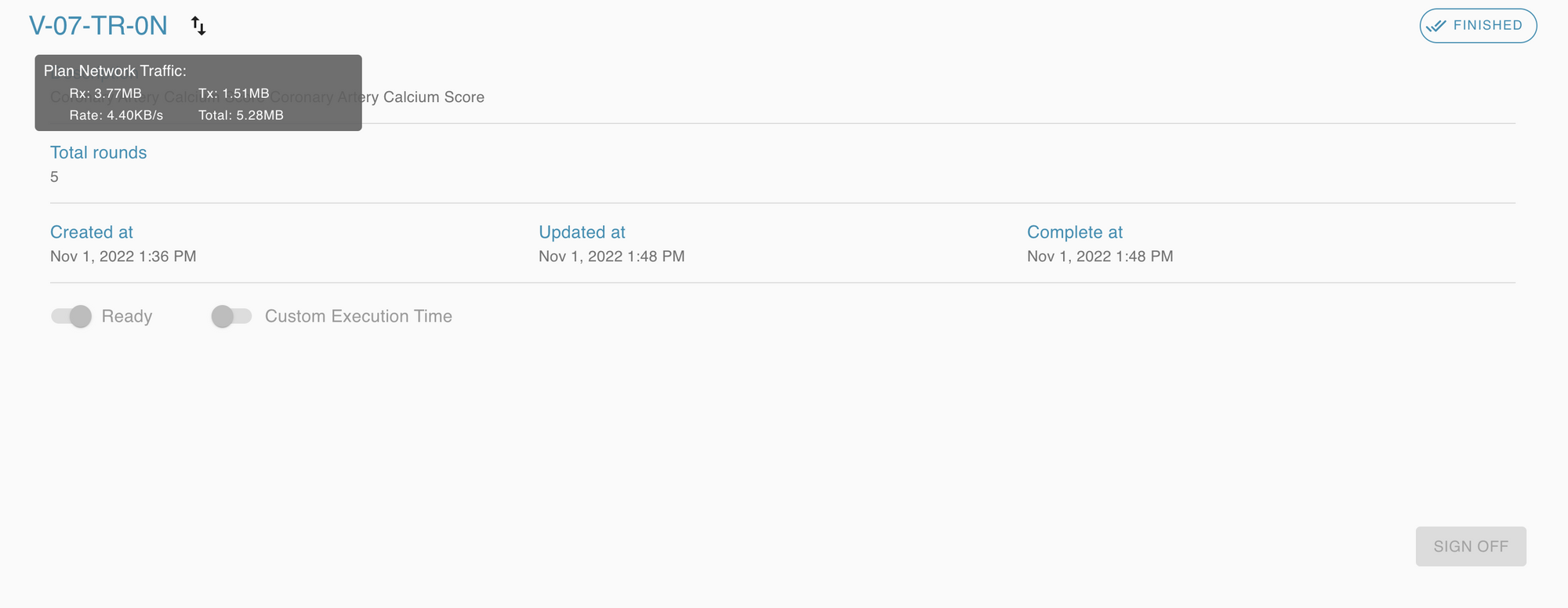
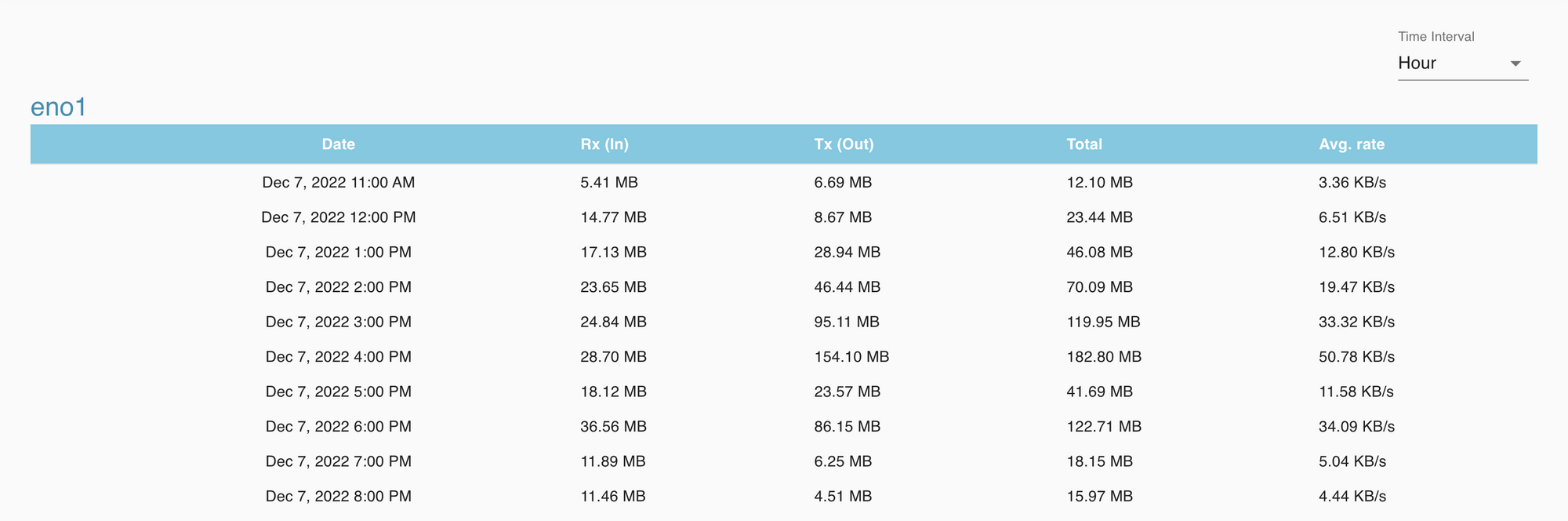
6. Log system, including Network Flow data monitoring system is provided for auditing.
PS: Users could see how much bandwidth were used during the pass period; or how much bandwidth, including in (Rx) /out (Tx) data flow amount, during a specific Federated Learning or Federated Validation plan.
Network Traffic real-time status:
Network Traffic usage review:
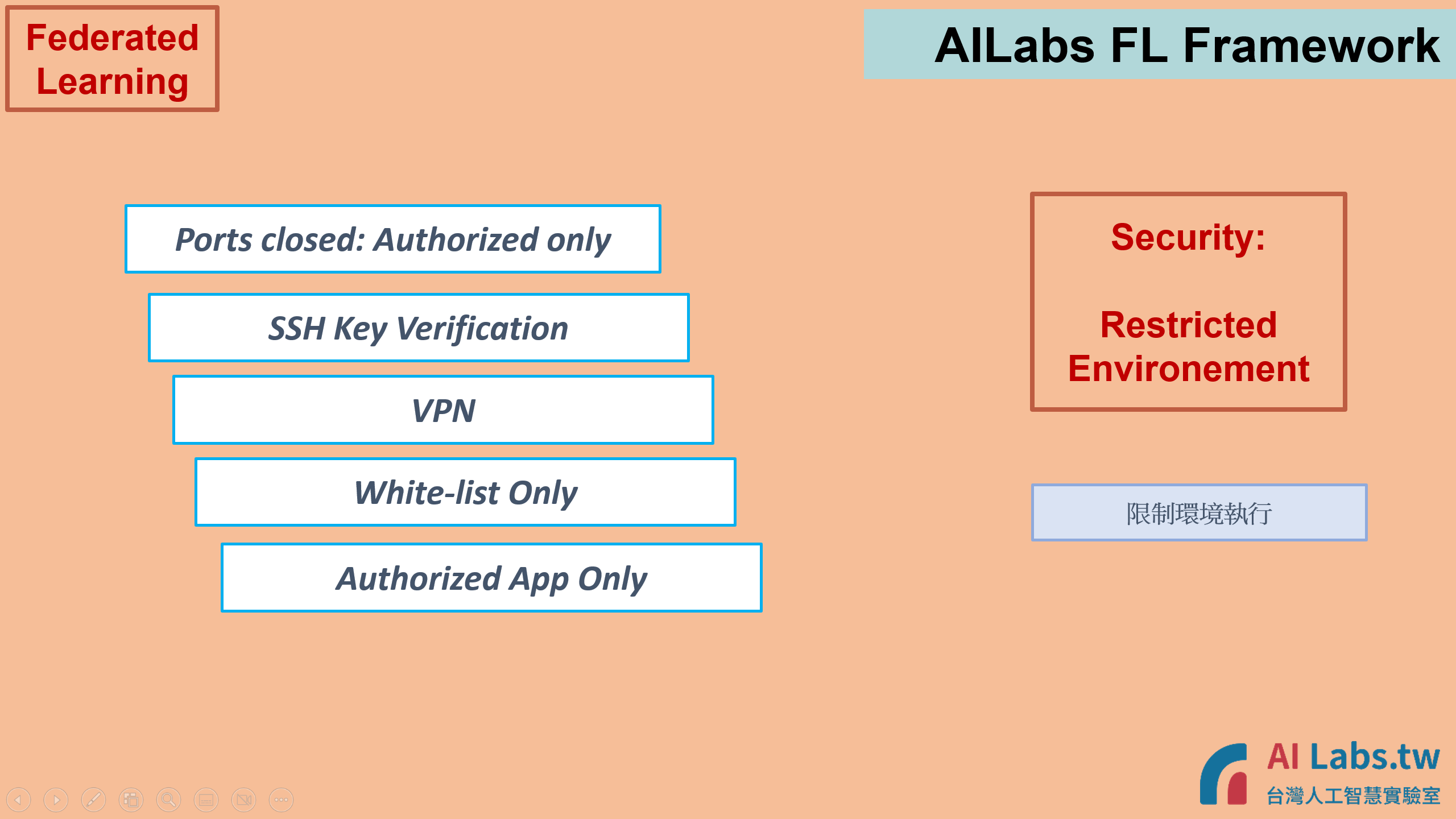
7. The framework restricts very limited authorization access to make sure the environment is secure. For example, the training progress will only through HTTPS (443) port only; no other ports need to be turned on the Institute's firewall.
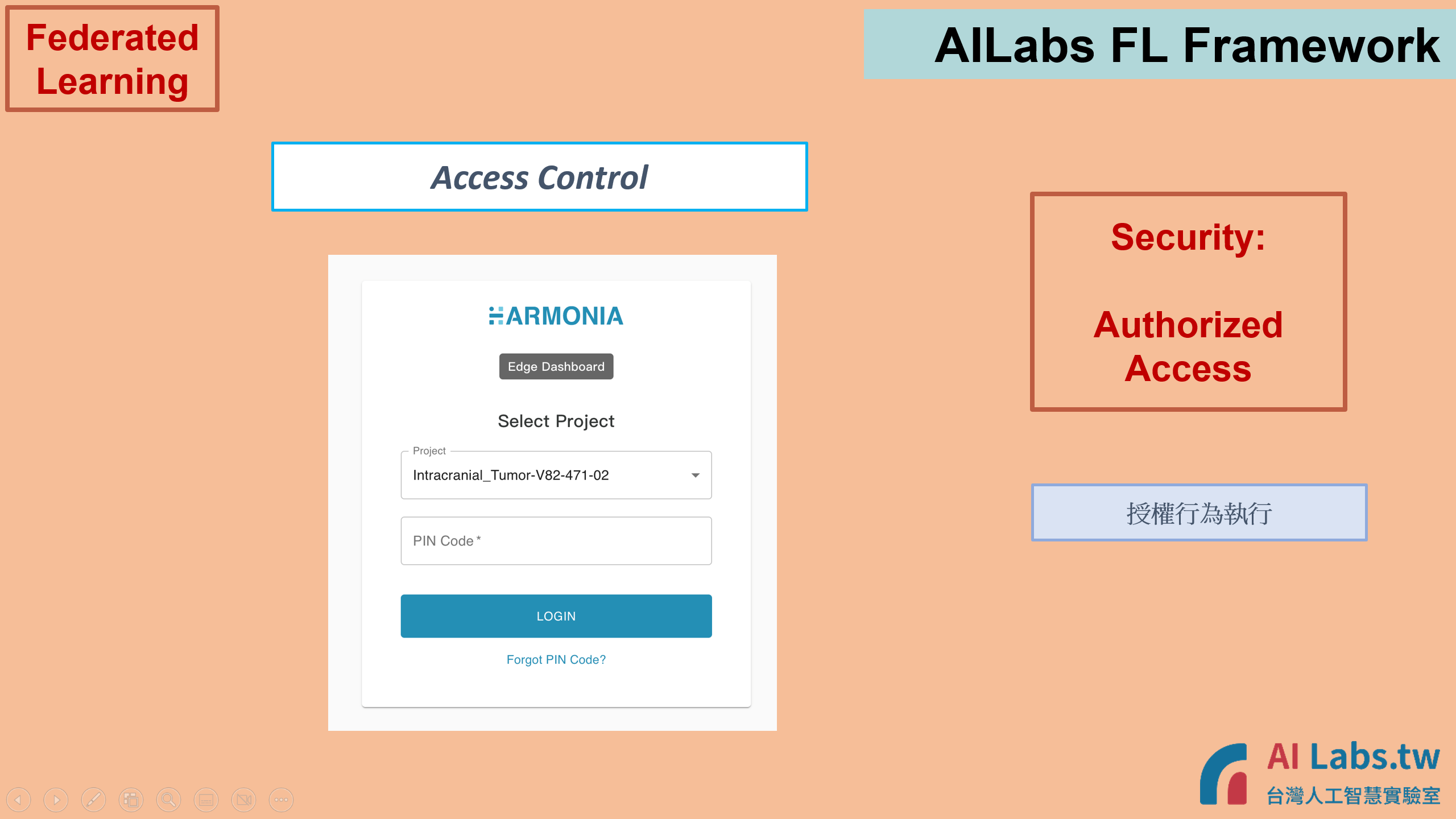
8. User account's access right is also limited for authorized actions only.
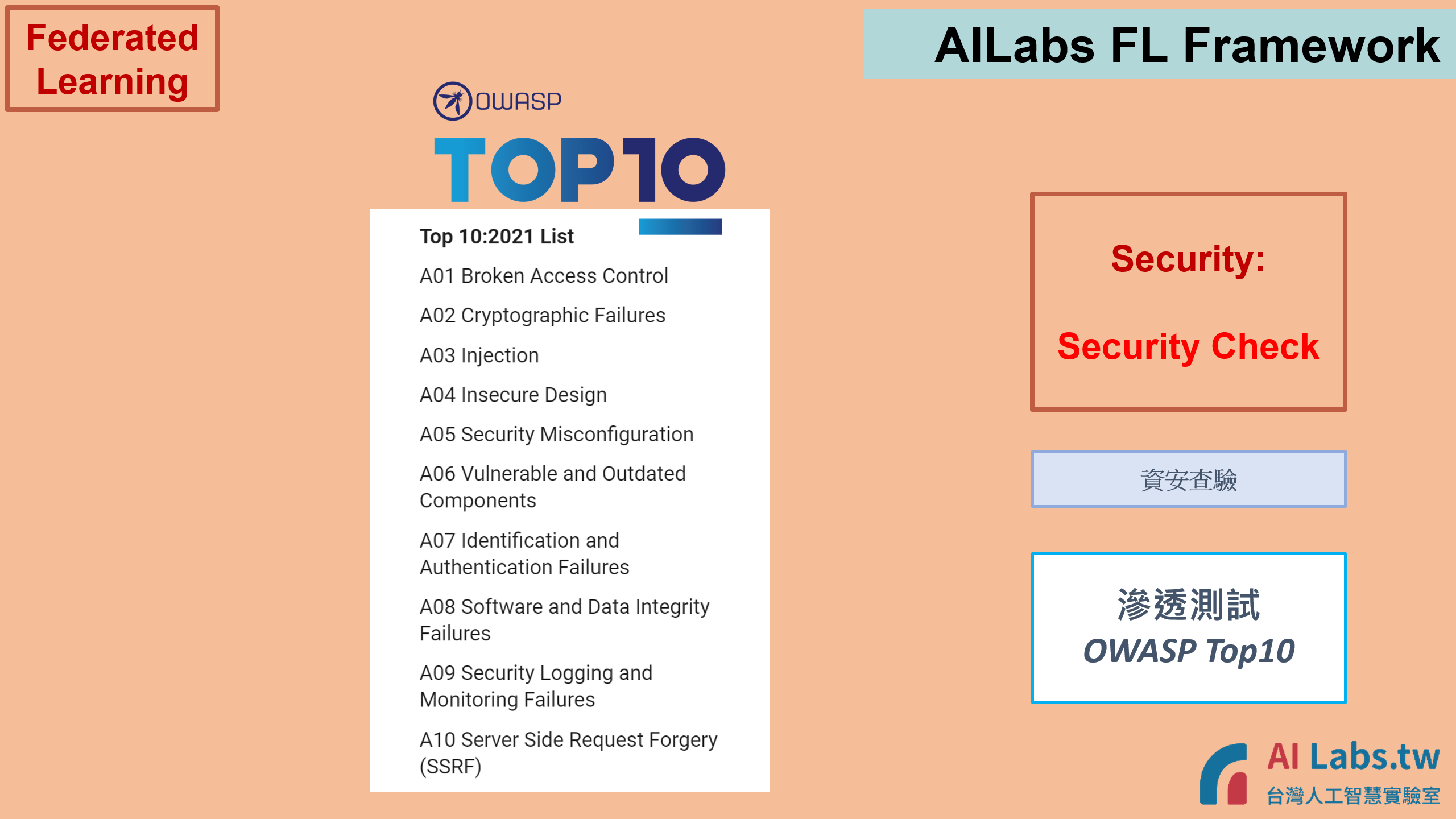
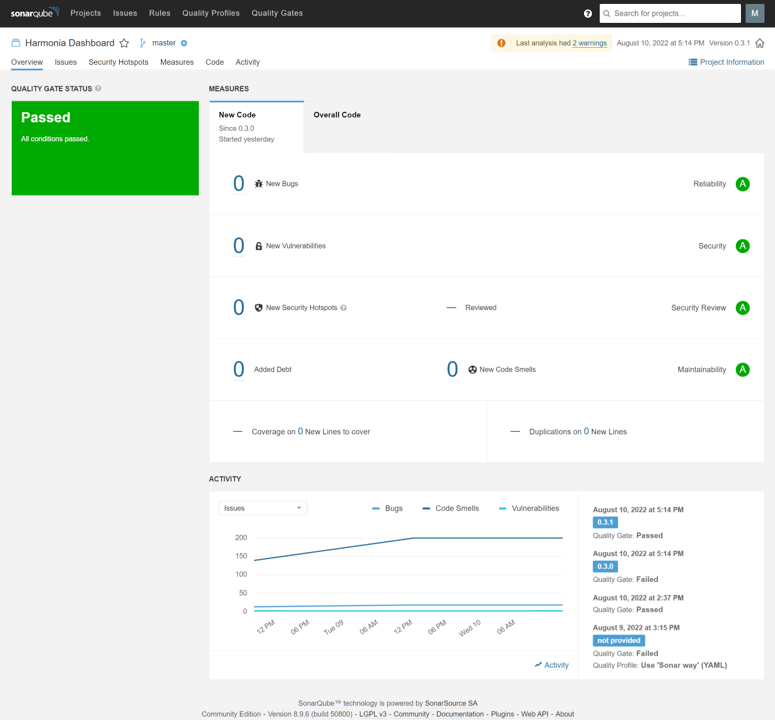
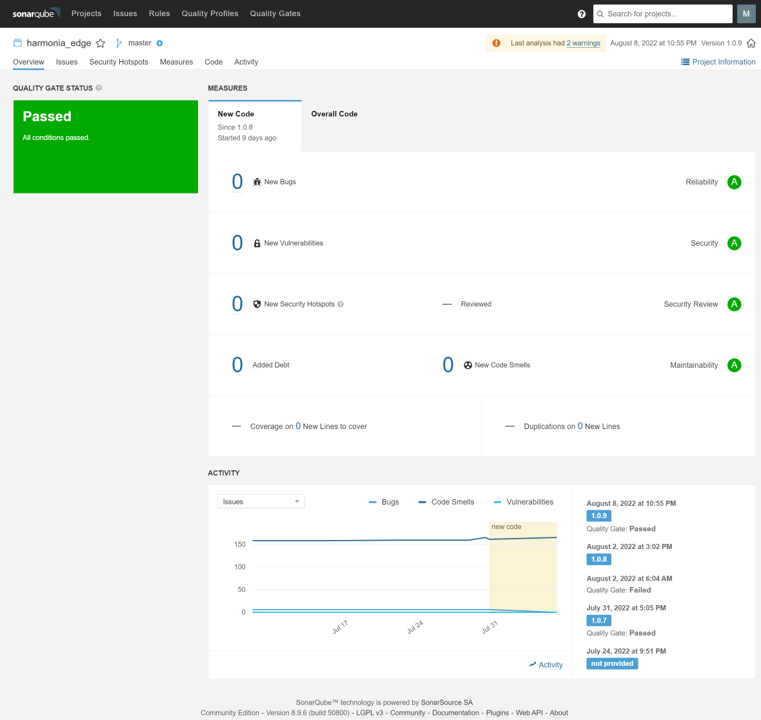
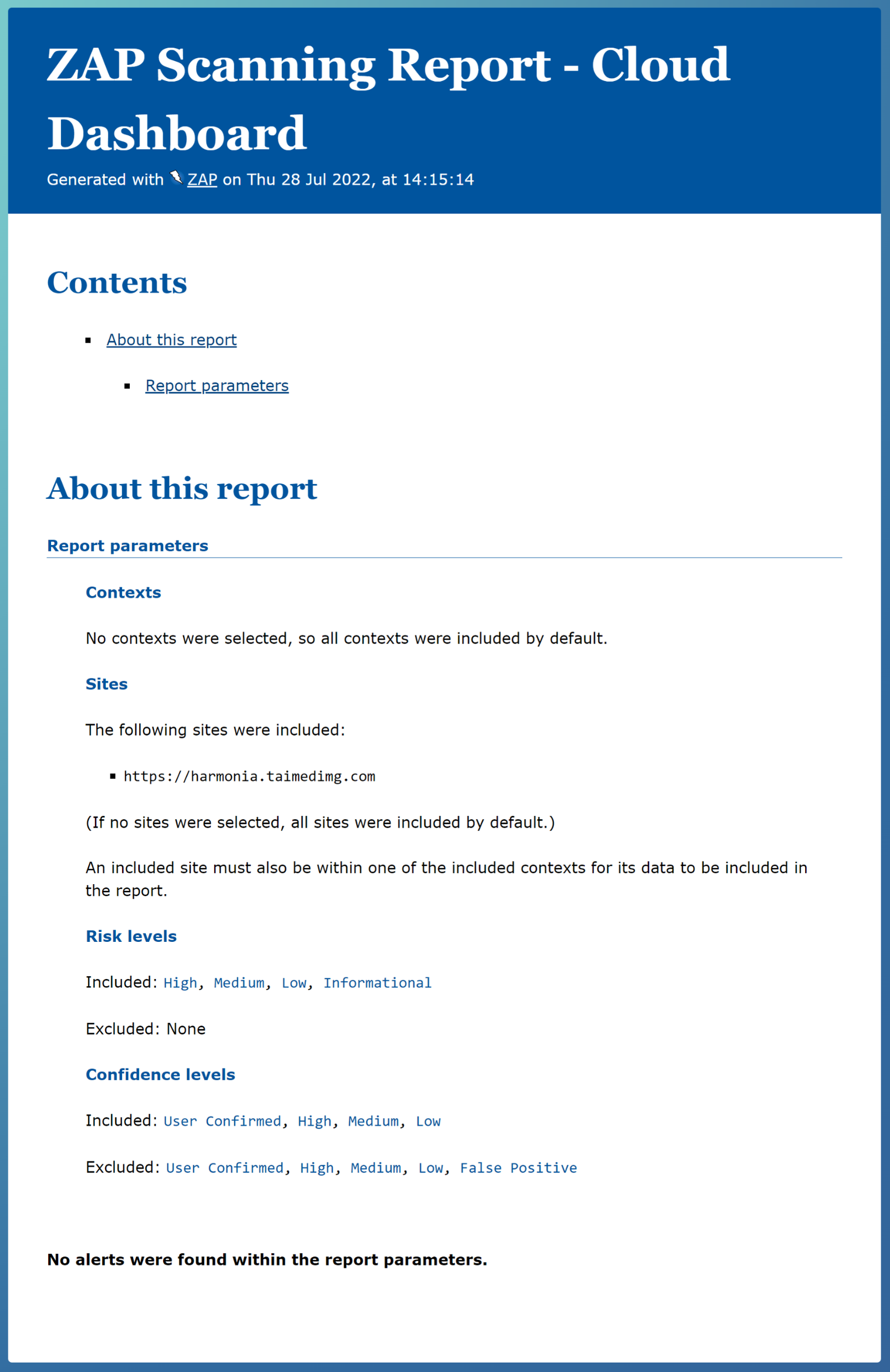
9. Diverse security checks implementation to ensure code security, environment security in all aspects!
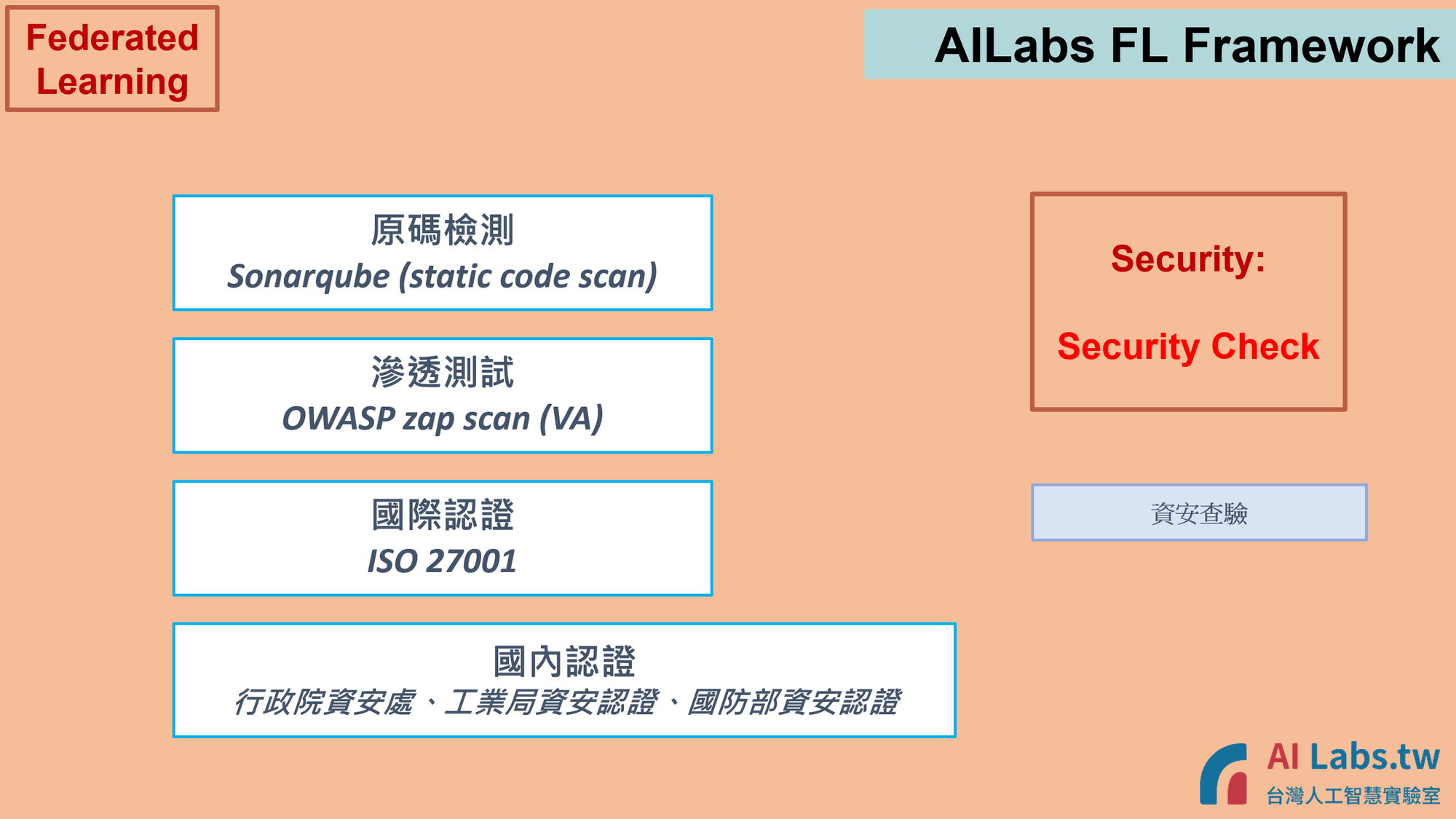
Static Application Security Testing (SonarQube Scanning Reports):
Dynamic Application Security Testing (ZAP Scanning Reports):
ISO Certificates:

Taiwan AI Labs Federated Learning Security Compliance Document: URL -
https://harmonia.taimedimg.com/flp/documents/fl/2.0/manuals/ch8/8-4-federated-learning-security-compliance